Smishing & Vshing techniques are back (actually, they haven’t gone away).
That’s what proves that the Internet isn’t the only compromised compromised place, full of crooks and criminals…
Along with phishing, these 2 common are also used by hackers to access our private information and steal money at their will.
To avoid fall into their trap, we first have to know what Smishing & Vshing are about.
What is the Smishing Technique?
I know… It sounds cute, but don’t let that fool you.
Smishing is basically the phishing scam through text-messages. The term was born as the combination of “SMS” and “phishing.
It has been around since the 90s, where telephonic communication became the mainstream norm.
But instant-messaging apps like WhatsApp, WeChat, or Apple’s iMessage perfectly replace it today.
Interestingly enough, no-one seems to know about Smishing and Vshing, even when everyone has smartphones nowadays… Making it especially dangerous.
Smishing attacks use misleading text messages to attract immediate attention and trick victims to take action on an offer or request, imitating a trustable person/organization.
David Rayhaw, a senior researcher at McAfee Labs, explains how it looks:
“You receive an SMS along these lines: ‘We’re confirming you’ve signed up for our dating service. You will be charged $2/day unless you cancel your order: [www.smishinglink.com].’
Some users would recognize the scam, but everyone does.
They understand and exploit the victim’s emotional touchpoints (fear of cell phone bills) to steal private information, or lead them to malware-downloading places.
In many cases, the “Smishermen” will message from a “5000” number (via email) instead of displaying an actual phone number.
Smishing Statistics
Again, hackers know a lot about us… Like the time we spend looking at our cellphones.
Experian reports that adults (18 to 24 years old) send more than 2,022 texts every month, (67 every day) on average… And receive 1,831 messages.
Also, a survey made by Pew Research found that only 32 percent of all smartphone users install antivirus software on their phones.
Should you worry about these numbers?
Smishing Techniques & Examples
Remember what I told you about Hackers being capable of manipulating us, posing as a company we trust?
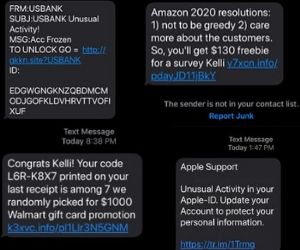
We could say someone well-prepared could pretend the role of an American Express (US bank) support contact to warn you about your credit card or account getting locked.
Other times… They can pretend to be Walmart with a clickable link to claim a $1,000 prize.
Or Amazon, giving away a $130 Gift Card just to answer a survey.
Even the “Apple Support” (ironically) recommending you to protect your device.
Is there any way to avoid a SMShing attack?
Too hard to avoid it in the first place, but it’s practically easy to not fall into their trap.
How to Prevent Being a Smishing Victim?
Take notes about the following tips to avoid fall into the smisher’s trap:
- Avoid “too good to be true” promotional messages.
- Do not trust unknown phone numbers.
- Do not provide personal or banking information through non-confidential channels (most times, they don’t ask for it through SMS).
- Do not follow to click a link sent from an unknown source.
- Only input your private information on safe websites (recognizable domain + https)
With all of it in mind, it will be too hard for hackers to catch you on their trap through SMS.
But what about phone calls? Is there any chance for them to use it with malicious intentions?
Yes, they do. In this case, the technique is called “Vshing”.
What is Vshing?
As mentioned, “Vishing” uses voice calls instead of emails (phishing) or texts (smishing). This term comes from “voice” + “phishing”.
In this case, the criminal relies on “social engineering” techniques to trick you into providing information that others can use to access and use your important accounts.
Most times, they achieve it in 2 different ways:
a) He/She impersonates the role of your banking entity, asking for your private credentials with the excuse of “checking” an issue.
b) He/She impersonates you by requesting support for the block of the account, a high-charge debt, or a similar urgent situation.
Both cases are extremely dangerous, and strangely effective if properly executed.
Take into account that when a criminal impersonates you, he/she will be using personal information (Address, Email, Phone number) easily found on the Internet/social media.
Sometimes. extreme measures are taken, with the use of human-sounding animated voices.
All of this is intended to get enough information to breach bank accounts, transferring money with your “consent” or to open new accounts at your behold.
Yes. This sounds risky and might result in somehow exaggerated… Has someone fallen on it?
Vishing Statistics
Vishing works even better than you think.
To give you an example, the manager of a UK energy company let cyber-criminals take £200,000 because of spoof voicemail powered by artificial intelligence that sounded like the manager’s boss.

But not only multi-million dollar companies are victims of it. The FTC has reported a $960 average loss for civilians who notified the government of being attacked.
Vishing attacks have been on the rise. And it shouldn’t surprise you that it will become widely recognized soon (for now, 25% of participants from a Proofpoint’s worldwide survey demonstrated to know the Vshing definition).
Vshing Techniques & Examples
If you are a great observer, you will notice a common pattern between all vishing attacks.
Almost all of them are made via voice over IP (VoIP) services, being easier to automate the process, and getting more to trace for both victims and law enforcers.
Also, practically all vshing calls try to harvest your personal or banking information, to profit one way or another. That would include cases like:
- Exaggerated investment opportunities
- Urgent Banking Changes
- Unsolicited offers for credit and loans
- Requests for Charitable causes
- Extended car warranty scam
Remember, they’re master at it. Their job is to seek every possible angle to convince you and get the exact information they need to steal you.
The mere thought of having a team of criminals behind your back for it it’s scary…
Is there something you can do?
How to Prevent Vishing Attacks?
Once again, you’re very fortunate to know that these types of attacks are also easy to avoid.
First of all, just starting becoming more aware of where your number phone is placed online.
If at any given moment, you receive a message or a call from an unknown number… Turn on your alarms (even if it’s nothing). But especially if they request personal information.
In those cases, take your time to think and ask whatever is needed.
You are not ready at the moment? Hang up and return the call when you feel like it.
In the meantime, you could research the number’s legitimacy.