Keyloggers look like taken out of spy movies… But they’re (unfortunately) real.
Hackers might lurk into your system, watching every one of your moves, waiting for you to give out valuable, private information… That’s the reality of keylogging.
They commit a keystroke by interfering at the moment you press a key, and when the data is displayed on the monitor.
Want to know more about it, how it works, and how to avoid it at all costs?
What are Keyloggers?
A keylogger basically tracks all data typed into your keyboard.
Keystroke logging mechanics are among the oldest type of spyware: history shows that the 70s presented the first keylogging devices for electric typewriters (named electric bug).
And it kept evolving through the 80s and 90s, where keylogger malware was developed.
Now, they don’t need to take physical measures to discover private information like credit card numbers, from victims across the world.
In most recent times, cybercriminals caught notorious attention through well-known events (keyloggers on HP laptops or the “debugging tools” inside a GTA V mod).
How do Keyloggers work?
It exists both as a spyware software (malware that doesn’t harm its host), and an internal hardware device (keyboard cable, USB or similar plugged in the CPU box).
Both records every button you tick-tack on the keyboard, believing nobody is watching.
Of course, the hardest to manipulate is the physical hardware. On the other hand, hackers use rootkit methods to succeed at infecting the victim’s device from distance…
For example, they find out you frequently visit sports news websites. So, they disguise the keylogger software as a fake attachment, inside a sports newsletter.
Innocently, you download it, expecting to see the most exciting sports news, but instead, it installs the keylogger inside your device.
Keyloggers tend to disguise through different forms, in different places:
a) Just as in the example, the victim clicks on the link or file inside a phishing email.
b) Exploiting vulnerable web browsers through scripts. The keylogger launches at every user’s visit.
c) It hosts inside the device through the infection of other malware.
Why is Hard to Avoid Keyloggers?
Keyloggers are everywhere. They’re extremely common nowadays.
That’s because not only hackers themselves use it to steal your banking information… But it’s also promoted by big companies in semi-legitimate and creepy ways.
- Husbands and Spouses use keyloggers to keep track of their loving partner.
- Governments themselves use keyloggers to keep track of protest groups and criminals, to later build cases.
- Employers use keyloggers to assure their workers are staying on task, or to avoid any unethical practices inside the workplace.
Basically, tech companies are capable of infiltrating into every aspect of our daily life, without heave consequences.
Microsoft is one of those that already use keyloggers, as a Windows 10 built-in feature.
What do IT security companies have to say about this?
The Kaspersky Lab has detected a considerable number of spy programs used every month (almost all of them possess keylogging tech features).
To put you on context: An approximate of 10 million computers in the US show signs of malware infection that runs as keyloggers alternatively.
This data comes from John Bambenek’s research (Analyst at the SANS Institute), where they calculate a loss of $24.3 million every year, due to e-payment systems breaches.
Here’s the scariest part: because there are plenty of “legitimate” uses for keyloggers, they aren’t tagged as illegal or unregulated, and you can even purchase them online.
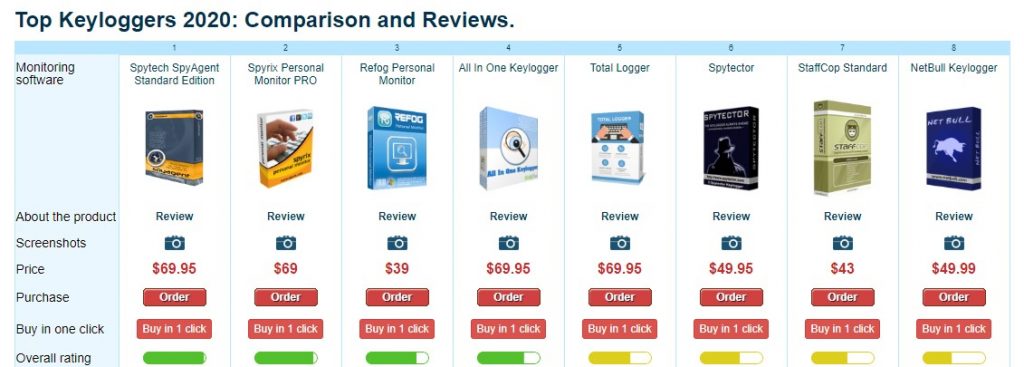
Because of that, not all antivirus programs detect keylogger as a threat.
But these programs don’t have to be frightening, after all.
Learn how to recognize, avoid, and remove them successfully.
How to Detect a Keylogger in your Device
Reality is, they’re very hard to detect once it is placed inside your computer. These tiny, lightweight programs may disguise as an ordinary browser extension.
Even, they may hide inside the computer’s firmware. This is efficient to them because firmware stays outside of the operating system (therefore, Anti-virus software cannot detect them.
This is the best way to detect if a Keylogger is logged into your device:
- Open the Task Manager (ctrl + alt + delete).
- Check between all the programs, if there’s a lightweight running with a suspicious name.
- Found one? You can find instructions on how to remove it by Googling its name.
- BUT WAIT… Advanced keyloggers can hide from the task manager, at least minutes later after the OS boots up. To detect any like it, open the Task Manager, and click on the tab “Startup”.
- Also, you can look up for malicious extensions on Google chrome browser that you didn’t install yourself (chrome://extensions in the URL).
Of course, it’s important to mention that there’s not just 1 type of keyloggers, but many.
They all use different techniques: some even manipulate the task manager, becoming undetectable.
These special situations require special measures as well.
How to Prevent Keyloggers from Stealing
It is better to avoid having one in the first place.
So you can consider the following tips to prevent keyloggers from stealing any valuable information out of you:
- Download files only trustable sources (NOT torrent or unknown email addresses).
- Use a virtual keyboard to allow communication without the actual need for physical keys. Especially when you’re entering information on high-risk sites like Banks.
- Voice-to-text software also avoids typewriting, therefore, keylogging chance.
- One-time password systems are highly effective against both keylogging software and hardware. You can keep it safe too with a password manager (the manager will automatically enter the password, making keystrokes redundant).
- Advanced anti-virus or dedicated anti-spyware software can be the perfect first line of defense.
- Application whitelisting is a great alternative that may save your life. With it, only specific programs are authorized to run on your system.
- Keep your Operative System and all your software up to date.
Proactive protection will protect currently existing, and incoming keyloggers from the future.
How to Remove Keyloggers Completely
Are you completely sure you have been a victim of keylogging?
Then it’s time to act. Delete it right away.
Although removing the keylogger completely for your own it’s not easy. It’s quite a headache.
But, because your private information is ultra-valuable… We can guarantee you peace of mind with a guided step-by-step IT support.