Cyberpunk 2077 Developer (CD Projekt Red) disclosed that they were the target of a ransomware attack that encrypted their network’s devices and led to the theft of files.
While they first tagged the bad actor as an “unidentified” one, it’s now well-known that the ransomware attack was conducted by the ransomware group named ‘HelloKitty.’
It has been tough months for the Polish company. And there are no stopping signs nearby.
Ransomware Against CD Projekt Red Source Code
The whole incident started with the announcement of the Cyberpunk 2077 developer disclosing what happened on Twitter:
Important Update pic.twitter.com/PCEuhAJosR
— CD PROJEKT RED (@CDPROJEKTRED) February 9, 2021
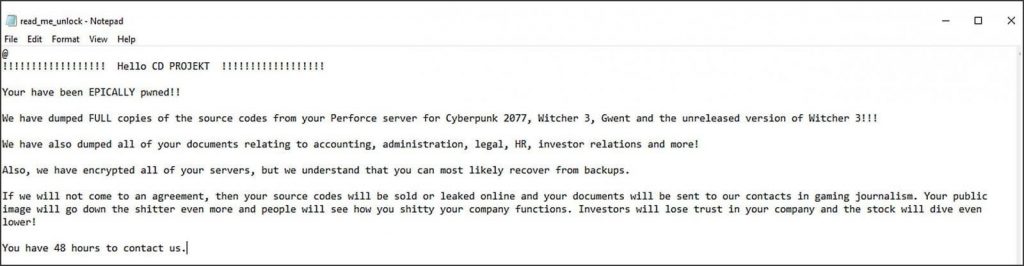
The letter on the left says:
“Yesterday we discovered that we have become a victim of a targeted cyberattack, due to which some of our internal systems have been compromised.
An unidentified actor gained unauthorized access to our internal network, collected certain data belong to CD PROJEKT capital group, and left a ransom note of the content of which we release to the public. Although some devices in our network have been encrypted, our backups remain intact. We have already secured our IT infrastructure and begun restoring the data.”
And the one shared at the right is nothing more and nothing less than the hacker’s ransom note, claiming to have stolen the source codes for Cyberpunk 2077, The Witcher 3, Gwent, as well as an “unreleased version” of The Witcher 3.
The message continued:
“We have also dumped all of your documents relating to accounting, administration, legal, HR, investor relations, and more.
“If we will not agree, then your source codes will be sold or leaked online and your documents will be sent to our contacts in gaming journalism.”
According to the hackers, they were capable of encrypting CD Projekt Red’s servers, but this was refused later on by the company, which argued their backups remained intact.
They also confirmed their IT infrastructure was rapidly secure, as well as it began restoring the data right away.
The media suggests this was a move from the company to defend against the perpetrator’s extortion attempts. They gave 48 hours to contact back and the studio replied:
“We will not give in to the demands nor negotiate with the actor, being aware that this may eventually lead to the release of the compromised data.”
CD Projekt Red added: “We’re taking the necessary steps to mitigate the consequences of data being leaked.”
But this isn’t an easy task to achieve on the internet. Someone by the name of ‘redengine’ created an auction on a hacker forum for the stolen data. This is a common practice for the monetization of ransomware attacks.
This auction started at $1 million, and sources assure bids were scaling to $500,000 each.
But there also was a “buy now” button (often called Blitz) for the price of $7 Million, for those who wanted to buy it immediately.
Although the attackers claimed to have supposedly sold the data outside the forum, there’s still no proof of this being true. At least no info about a purchaser has been publicly displayed and also no personal player’s data has been compromised on this event.
The company keeps investigating the case with the authorities and they’re taking as many security measures as possibles, including a delay on the anticipated Patch 1.2 of Cyberpunk 2077, which contains bug fixes and performance improvements.
They explained more details about it throughout several tweets:
“While we dearly wanted to deliver Patch 1.2 for Cyberpunk 2077 in the timespan we detailed previously, the recent cyberattack on the studio’s IT infrastructure and extensive scope of the update mean this, unfortunately, will not happen — we’ll need some additional time.”
“Our goal for Patch 1.2 goes beyond any of our previous updates. We’ve been working on numerous overall quality improvements and fixes, and we still have work to do to make sure that’s what you get. With that in mind, we’re now aiming for release in the second half of March..”
“It’s not the news we enjoy sharing, but we want to make sure we launch this update properly. Stay tuned for more information as the time draws closer. Thank you for your continued patience and support.”
What No-One Knew About the HelloKitty Malware Gang
Now, we can’t finish this piece without talking about the malware gang with such a controversial name.
The good news is, the HelloKitty malware is not active right now but is for the most part because there’s almost no information about the threat itself.
Cybersecurity experts only know one thing: that it was named after a used mutex (HelloKittyMutex) on the malware’s executable launch.
Once launched, it repeatedly runs taskkill.exe to target and terminate over 1,4000 security-associated processes and services: email and database servers, as well as backup and accounting software.
It shuts down them all and continues to encrypt computer files. Then, it attaches a .crypted extension to the file’s name
This ransomware gang has been active since November 2020, targeting companies such as the Brazilian power company CEMIG last year. And this wouldn’t be the first videogame maker to receive cybersecurity damages, last year, we saw Ubisoft and Capcom, as well.